
Enhancing Secure Remote Access for IT and OT Environments
Dec 15, 2025
/
Onur Semih SEVİM
In today’s interconnected digital world, IT and OT systems increasingly require seamless yet secure remote access solutions. Traditional VPN-based methods, while prevalent, often fall short in meeting modern security and operational demands. This blog explores how Privileged Access Management (PAM) solutions can address these challenges with innovative approaches tailored for hybrid IT and OT environments.

1- Secure and VPNless Access for Third-Party Users
Third-party vendors and service providers are consistently cited as one of the most common entry points for cyberattacks. VPN-based access typically grants broad network-level connectivity, which increases the blast radius if credentials are compromised. In contrast, a PAM-enabled, VPNless access model shifts the focus from network access to identity- and session-based access.
With PAM, third-party users are granted access only to the specific systems and functions required to perform their tasks. Sessions are established without exposing the internal network, dramatically reducing lateral movement risk. Every connection can be monitored and recorded in real time, enabling organizations to meet regulatory requirements and quickly investigate suspicious behavior. This approach not only strengthens security but also simplifies onboarding and offboarding of external users without the operational overhead of managing VPN accounts.
2- Secure and VPNless Access for Privileged Users
Privileged users such as system administrators, engineers, and operators require fast and reliable access to critical infrastructure. However, standing privileges and persistent VPN connections significantly increase exposure to credential theft and misuse. PAM addresses this challenge by enforcing least privilege and time-bound access without sacrificing usability.
Through Just-in-Time access, privileged rights are granted only when needed and automatically revoked once the task is complete. All sessions are encrypted, continuously monitored, and correlated with user identity, providing strong accountability. Integrated multi-factor authentication and centralized identity management further reduce reliance on static credentials. The result is a streamlined user experience that improves productivity while materially lowering the risk of insider threats and compromised accounts.
3- Extending Remote Access to OT Sites and Plants via Connectors
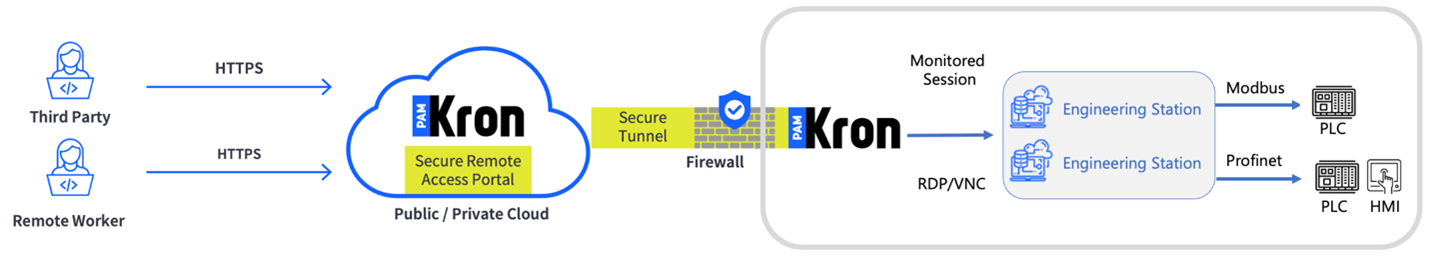
Connecting IT and OT environments introduces unique challenges, including strict network segmentation, legacy systems, and OT-specific protocols. Traditional remote access tools often struggle in these environments, leading to insecure workarounds or excessive firewall exposure. PAM-enabled connectors provide a purpose-built solution by acting as secure gateways between users and OT assets.
These connectors are designed to work with industrial protocols and segmented networks without requiring inbound connections to critical OT systems. Access policies can be centrally defined and enforced across geographically distributed plants, while all sessions are logged and monitored from a single control plane. This approach allows organizations to maintain strong security boundaries while still enabling the remote operations and maintenance that modern industrial environments demand.
4- Secure Remote Access for OT Contractors Using PAM

OT contractors frequently require temporary, highly controlled access to industrial systems, often from remote locations with limited bandwidth. VPN-based solutions are poorly suited to these scenarios, as they are bandwidth-intensive and difficult to manage securely at scale. PAM platforms address this gap by enabling controlled IP and port-level tunneling without exposing the broader OT network.
These connections are optimized for low-bandwidth environments and provide fine-grained control over what contractors can access and for how long. Every action is auditable, creating a clear trail for compliance, safety investigations, and regulatory reporting. This ensures that organizations can collaborate effectively with external specialists while maintaining strict governance over critical OT environments.
Modern IT and OT environments demand secure, efficient, and user-friendly remote access solutions. By leveraging secure privileged access systems like Kron PAM, organizations can eliminate the vulnerabilities of VPNs, ensure compliance, and enhance operational efficiency. Whether it’s third-party vendors, privileged users, or OT contractors, a PAM-enabled approach provides the tools necessary for secure access across diverse environments.
*Written by Onur Semih Sevim. He is a Head of Europe & LATAM Sales at Kron.


















