
Multi-Tenant Privileged Access Management for MSPs and MSSPs
Feb 17, 2026
/
Onur Semih SEVİM
Securing Customer Environments at Scale Without Operational Overhead
For MSPs and MSSPs, privileged access management is no longer just an internal security control - it is a regulatory requirement, a contractual expectation, and a trust differentiator. Frameworks such as NIS2, DORA, the Cyber Resilience Act, SOC 2, and the UK Cyber Security and Resilience Bill increasingly hold service providers accountable not only for their own access controls, but for how privileged access is governed across every customer environment they touch.
Meeting these requirements with enterprise-centric PAM platforms often introduces the very risks MSPs and MSSPs are trying to avoid: shared infrastructure, weak tenant isolation, operational sprawl, and high cost-to-serve per customer.
Kron PAM’s multi-tenant-by-design architecture directly addresses these challenges. It enables service providers to deliver PAM as a secure, compliant, and scalable managed service, rather than a fragmented collection of customer-specific deployments.
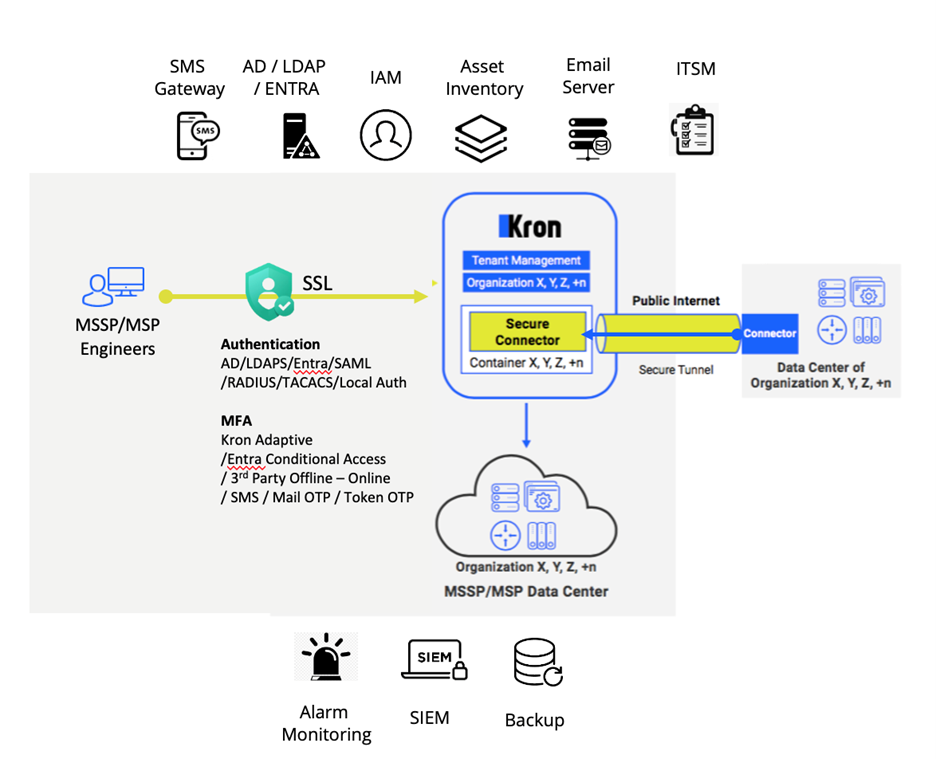
Overview
Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs) operate in uniquely complex environments. They are responsible for securing privileged access across multiple customers, multiple infrastructures, and multiple trust boundaries - often with vastly different regulatory, operational, and security requirements.
Traditional PAM solutions, designed for single-enterprise use, struggle in MSP/MSSP contexts due to:
- Poor tenant isolation
- Complex infrastructure requirements
- Heavy operational overhead
- Limited support for third-party and just-in-time access models
A modern multi-tenant PAM architecture must enable service providers to securely manage privileged access across all customer environments, while preserving strict isolation, scalability, and operational efficiency.
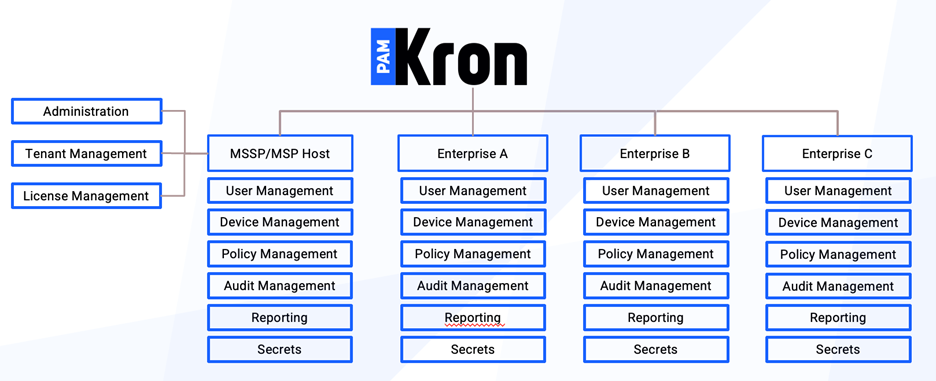
This post outlines how a multi-tenant PAM approach enables MSPs and MSSPs to:
- Enforce least-privilege access across all customers
- Secure internal engineers and external vendor access
- Meet regulatory and contractual obligations
- Scale PAM operations without multiplying infrastructure or cost
Tenant-Aware Asset & Privileged Access Discovery
MSPs and MSSPs manage hundreds of customer environments, each with its own assets, credentials, and ownership boundaries. A multi-tenant PAM must maintain clear separation while enabling centralized oversight.
Tenant-Scoped Discovery Capabilities
A multi-tenant PAM platform supports flexible discovery methods per customer:
- Network-based discovery to identify reachable systems and management interfaces
- Directory-based discovery (AD, Entra ID, LDAPS) per tenant
- Bulk imports for rapid onboarding of new customers
- CMDB integrations to align asset ownership, service tiers, and SLAs
Each discovered asset is:
- Explicitly mapped to a tenant
- Isolated from other customers by design
- Governed by tenant-specific policies and access controls
This ensures zero cross-customer visibility or access leakage, a foundational requirement for service providers.
Multi-Tenant Identity & Administration Model
Strong Tenant Isolation
A multi-tenant PAM architecture enforces logical and cryptographic separation between customers:
- Dedicated tenants for each customer environment
- Independent policy sets, credential vaults, and audit logs
- No shared access paths or administrative bleed-over
Flexible Identity Integration
Each tenant can integrate with its own identity source:
- Entra ID, Active Directory, or SAML-based IdPs
- Tenant-specific MFA and conditional access policies
- Support for shared MSP identities with tenant-scoped authorization
This enables:
- MSP engineers to access multiple customers without credential reuse
- Customers to retain full control over their own identity governance
- Clean separation between provider admins and customer admins
Policy-Driven Privileged Access Across Customers
A multi-tenant PAM allows MSPs and MSSPs to enforce consistent security standards, while respecting customer-specific requirements.
Centralized Policy Framework
Policies can be defined at multiple levels:
- Global (provider-wide baseline controls)
- Per tenant (customer-specific requirements)
- Per role, system type, or access method
Policies may include:
- MFA enforcement
- Time-bound and just-in-time access
- IP and geo-based restrictions
- Manager or customer approval workflows
- ITSM ticket validation per tenant
- Role-based access with least-privilege enforcement
All policies are enforced without scripting and applied uniformly across environments.
Secure Remote Access via Tenant-Dedicated Gateways
MSPs and MSSPs must provide privileged access to customer environments without exposing networks, without shared VPNs, and without breaking tenant isolation. A multi-tenant PAM architecture achieves this through tenant-specific connectivity gateways deployed within each customer environment.
Tenant-Dedicated Inbound Connectivity
For each customer, a lightweight PAM gateway/connector is deployed on-site or within the customer’s cloud environment:
- One or more tenant-bound gateways per customer
- Outbound-only, encrypted connections initiated from the customer site
- No inbound firewall rules or exposed management interfaces
- Gateways are cryptographically bound to a single tenant
This ensures strict separation between customer environments and eliminates shared access paths.
Secure Session Brokering Without Network Exposure
All privileged sessions are brokered through the tenant gateway:
- The multi-tenant PAM platform performs identity validation and policy decisions
- Approved sessions are securely routed to the customer gateway
- The gateway establishes the connection to the target system locally
The PAM platform never directly connects to customer assets, preserving network sovereignty and zero-trust principles.
Seamless End-User Experience at Scale
Simple Onboarding
Users onboard quickly without operational friction:
- SAML SSO into the PAM portal
- MFA registration per tenant or identity provider
- Native client/protocol access (SSH, RDP, etc.)
Guided Access
Users only see:
- The tenants they are authorized for
- The systems and access methods permitted by policy
- Active or approved access windows
Credentials are never exposed:
- Passwords and keys remain securely vaulted
- Access is injected dynamically at session time
- Credential rotation and lifecycle are fully automated
Centralized Logging, Audit & Customer-Ready Reporting
Tenant-Isolated Audit Trails
Each tenant receives:
- Full session recordings
- Indexed commands and keystrokes
- Tamper-proof audit data
Provider-Level Oversight
MSPs and MSSPs maintain:
- Centralized visibility across all tenants
- Cross-tenant analytics and health monitoring
- SLA, compliance, and access usage reporting
This supports:
- Regulatory compliance (SOC 2, NIS2, CRA, DORA, UK CSRB)
- Customer audits and contractual reporting
- Incident investigation and forensic readiness
Why Multi-Tenant PAM Matters for MSPs and MSSPs
A purpose-built multi-tenant PAM platform enables service providers to deliver secure, compliant, and scalable privileged access as a core service - without inflating infrastructure or operational costs.
Key Benefits
- True tenant isolation by design
- Scales from small customers to large enterprises
- Secure internal and third-party access
- Strong AAA, identity, and policy enforcement
- Full session visibility and audit readiness
- Lightweight, agentless deployment
Whether managing dozens or thousands of customer environments, a modern multi-tenant PAM ensures every privileged session is secure, governed, and fully observable - without slowing service delivery.
*Discover the solutions our TACACS+ RADIUS product offers for UK’s Telecommunications Security Act (TSA) and review them now.
Highlights
Other Blogs



















