
Unveiling the Crucial Role of Privileged Access Security and Governance in NIS2 Compliance
Mar 14, 2024
/
Kron
To prepare your organization for the upcoming NIS2, it is crucial to acknowledge that human factors play a pivotal role in cybersecurity. While focusing on the core aspects of cybersecurity processes, policies, and practices, it is essential to delve into understanding and addressing the multifaceted dimensions of identity security. As you explore our insightful guide, you will gain a comprehensive understanding of the background and objectives of NIS2. Discover how implementing a Privileged Access Security and Governance program can empower your organization to meet the essential requirements outlined in NIS2 Article 21. This includes incident handling and reporting, fortifying supply chain security, navigating cryptography and encryption technologies, shaping effective access control policies, and embracing a zero-trust security approach. Prepare your organization for the evolving landscape of cybersecurity with strategic insights and actionable solutions outlined in this resource.
What is NIS2?
NIS2 is a pivotal cybersecurity directive seeking to fortify critical infrastructure and digital services in the EU. Replacing the 2016 NIS Directive, NIS2 was adopted in November 2022. It mandates a high common level of cybersecurity across the EU, necessitating strategic adoption by member states and enterprises before October 17, 2024.
Enforcement and Penalties
NIS2 brings forth a new framework that entails penalties for entities failing to comply. Essential entities may face a maximum fine of no less than €10,000,000 or 2% of their total global annual turnover from the previous financial year, whichever is greater. For important entities, NIS2 mandates Member States to establish a maximum fine of no less than €7,000,000 or a minimum of 1.4% of the total global annual turnover from the preceding financial year, choosing the higher of the two.
What is the New Classification?
NIS2 introduces a transformative approach by categorizing entities as either “essential” or “important,” indicating the criticality of their services and their scale. In formulating cybersecurity strategies, Member States are urged to consider the risk exposure of these entities in terms of their societal and economic impact in the event of a successful cyberattack. For entities classified as essential, a comprehensive regulatory framework is established, entailing audits, on-site inspections, and off-site supervision. These entities are required to furnish documented cybersecurity policies, grant access to relevant data and documents, and provide evidence of policy implementation. Member States are obligated to empower competent authorities with enforcement capabilities, including issuing warnings, issuing instructions, appointing monitoring officers, suspending certifications, and more. In cases where these measures prove ineffective, the authorities have the authority to temporarily relieve leadership, including CEOs and legal representatives, of their managerial responsibilities. In the case of entities classified as important, similar enforcement tools are available, albeit with a more lenient approach. Regulatory bodies will offer recommendations on how compliance gaps can be addressed.
What Sectors Are Impacted by NIS2?
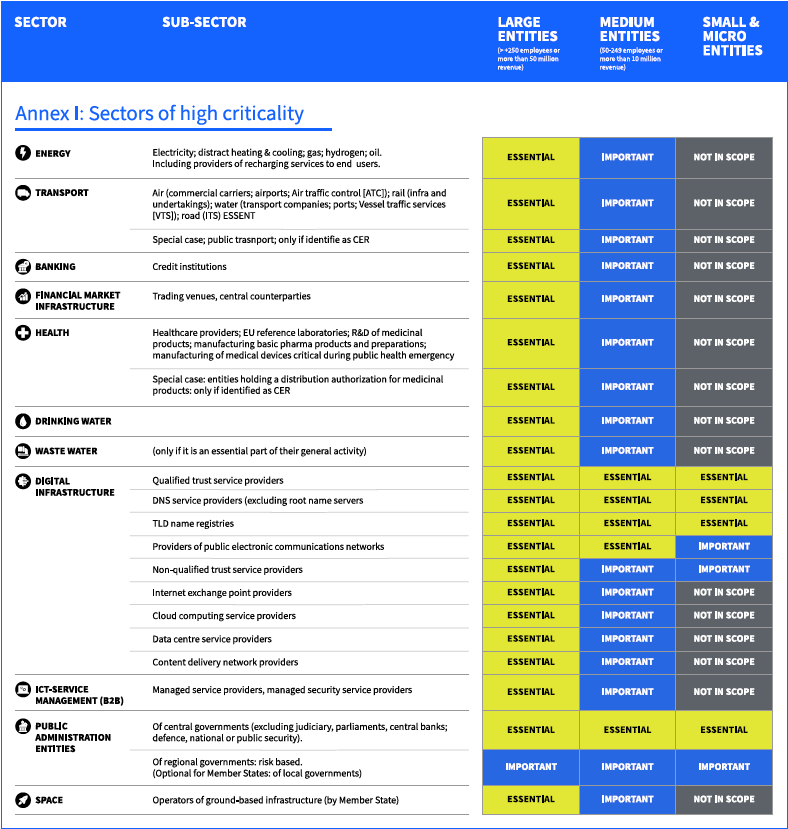
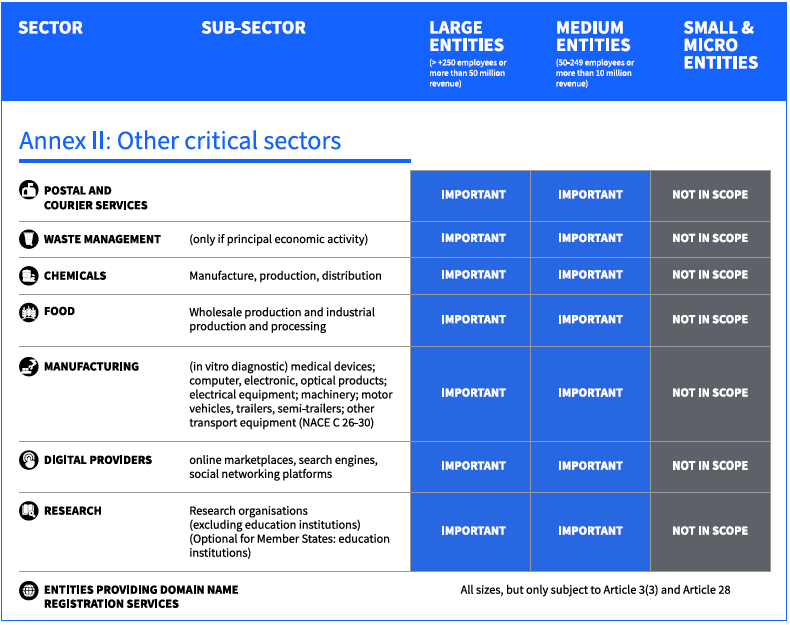
10 Minimum Cybersecurity Risk Measure
This proactive stance necessitates the adoption of a comprehensive, allencompassing approach geared towards safeguarding both the network and information systems, as well as the physical environment surrounding these systems. Essential components of this approach should encompass, but not be limited to, the following:
- Risk assessments and security policies for information systems
- Policies and procedures for evaluating the effectiveness of security measures.
- Policies and procedures for the use of cryptography and, when relevant, encryption.
- A plan for handling security incidents.
- Security around the procurement of systems and the development and operation of systems. This means having policies for handling and reporting
vulnerabilities. - Cybersecurity training and basic cyber hygiene practices including regular software and hardware updates, password rotations, management of new installations, restriction of administrator-level access accounts, integration of zero-trust principles, and systematic data backups - enable a proactive framework of preparedness and overall safety and security in the event of incidents or cyber threats.
- Security procedures for employees with access to sensitive or important data, including policies for data access. Affected organizations must also have an overview of all relevant assets and ensure that they are properly utilized and handled.
- A plan for managing business operations during and after a security incident. This means that backups must be up to date. There must also be a plan for ensuring access to IT systems and their operating functions during and after a security incident. The use of multi-factor authentication, continuous authentication solutions, voice, video, and text encryption, and encrypted internal emergency communication, when appropriate.
- Security around supply chains and the relationship between the company and direct supplier. Companies must choose security measures that fit the vulnerabilities of each direct supplier. And then companies must assess the overall security level for all suppliers.
A PAM-centric Review of the NIS2 Requirements
In the ever-evolving landscape of cybersecurity, the importance of a Privileged Access Management (PAM) solution becomes paramount in meeting the
stringent requirements outlined in the Network and Information Systems Directive (NIS2). The directive underscores the critical role of Computer Security Incident Response Teams (CSIRTs) in safeguarding essential and important entities against cyber threats. Particularly, PAM is highlighted in Paragraph 44, emphasizing its relevance in managing risks associated with supply chain compromises and critical vulnerabilities. Furthermore, PAM aligns with Paragraph 49’s focus on cyber hygiene practices, providing a foundational framework for protecting network infrastructures. As the directive extends its reach to address security concerns in the utility sector and supply chain, the implementation of a robust PAM solution emerges as a key element in fortifying entities against cyberattacks. In essence, PAM not only supports compliance with NIS2 requirements but also serves as a linchpin for enhancing overall cybersecurity posture and resilience.
CSIRTs capabilities including PAM and cyber hygiene practices
(Paragraph 44) The CSIRTs should have the ability, upon an essential or important entity’s request, to monitor the entity’s internet-facing assets, both on and off premises, in order to identify, understand and manage the entity’s overall organisational risks as regards newly identified supply chain compromises or critical vulnerabilities. The entity should be encouraged to communicate to the CSIRT whether it runs a privileged management interface, as this could affect the speed of undertaking mitigating actions.
(Paragraph 49) Cyber hygiene policies provide the foundations for protecting network and information system infrastructures, hardware, software and online application security, and business or end-user data upon which entities rely. Cyber hygiene policies comprising a common baseline set of practices, including software and hardware updates, password changes, the management of new installs, the limitation of administrator-level access accounts, and the backing-up of data, enable a proactive framework of preparedness and overall safety and security in the event of incidents or cyber threats. ENISA should monitor and analyse Member States’ cyber hygiene policies.
Utility Sector Security
(Paragraph 53) Utilities are increasingly connected to digital networks in cities, for the purpose of improving urban transport networks, upgrading water supply and waste disposal facilities and increasing the efficiency of lighting and the heating of buildings. Those digitalised utilities are vulnerable to cyberattacks and run the risk, in the event of a successful cyberattack, of harming citizens at a large scale due to their interconnectedness. Member States should develop a policy that addresses the development of such connected or smart cities, and their potential effects on society, as part of their national cybersecurity strategy.
Ransomware Protection
(Paragraph 54) In recent years, the Union has faced an exponential increase in ransomware attacks, in which malware encrypts data and systems and demands a ransom payment for release. The increasing frequency and severity of ransomware attacks can be driven by several factors, such as different attack patterns, criminal business models around ‘ransomware as a service’ and cryptocurrencies, ransom demands, and the rise of supply chain attacks. Member States should develop a policy addressing the rise of ransomware attacks as part of their national cybersecurity strategy.
Supply Chain Security
(Paragraph 85) Addressing risks stemming from an entity’s supply chain and its relationship with its suppliers, such as providers of data storage and processing services or managed security service providers and software editors, is particularly important given the prevalence of incidents where entities have been the victim of cyberattacks and where malicious perpetrators were able to compromise the security of an entity’s network and information systems by exploiting vulnerabilities affecting third-party products and services. Essential and important entities should therefore assess and take into account the overall quality and resilience of products and services, the cybersecurity risk-management measures embedded in them, and the cybersecurity practices of their suppliers and service providers, including their secure development procedures. Essential and important entities should in particular be encouraged to incorporate cybersecurity risk management measures into contractual arrangements with their direct suppliers and service providers. Those entities could consider risks stemming from other levels of suppliers and service providers.
Cyber Hygiene Practices
(Paragraph 89) Essential and important entities should adopt a wide range of basic cyber hygiene practices, such as zero-trust principles, software updates, device configuration, network segmentation, identity and access management or user awareness, organise training for their staff and raise awareness concerning cyber threats, phishing or social engineering techniques. Furthermore, those entities should evaluate their own cybersecurity capabilities and, where appropriate, pursue the integration of cybersecurity enhancing technologies, such as artificial intelligence or machine-learning systems to enhance their capabilities and the security of network and information systems.
Mandatory Incident Reporting
(Paragraph 102) Where essential or important entities become aware of a significant incident, they should be required to submit an early warning without undue delay and in any event within 24 hours. That early warning should be followed by an incident notification. The entities concerned should submit an incident notification without undue delay and in any event within 72 hours of becoming aware of the significant incident, with the aim, in particular, of updating information submitted through the early warning and indicating an initial assessment of the significant incident, including its severity and impact, as well as indicators of compromise, where available.
A final report should be submitted not later than one month after the incident notification. The early warning should only include the information necessary to make the CSIRT, or where applicable the competent authority, aware of the significant incident and allow the entity concerned to seek assistance, if required. Such early warning, where applicable, should indicate whether the significant incident is suspected of being caused by unlawful or malicious acts, and whether it is likely to have a cross-border impact. Member States should ensure that the obligation to submit that early warning, or
the subsequent incident notification, does not divert the notifying entity’s resources from activities related to incident handling that should be prioritised, in order to prevent incident reporting obligations from either diverting resources from significant incident response handling or otherwise compromising the entity’s efforts in that respect. In the event of an ongoing incident at the time of the submission of the final report, Member States should ensure that entities concerned provide a progress report at that time, and a final report within one month of their handling of the significant incident.
Kron’s Core Capabilities for Establishing a Solid Foundation for NIS2 Compliance
Digital secure vault: Securely stores credentials, passwords, certificates, secrets, and confidential data. Automatically changes all privileged credentials at regular intervals on different platforms and eliminates stale passwords.
Least privilege management: Centrally manages who can access critical systems and limits what they can do without any updates on critical systems or user computers.
Zero trust access: Implements a zero-trust model for privileged users connecting to internal resources, ensuring that only authorized users
gain access.
Required levels of trust: Ensures privileges are used only for legitimate business purposes by establishing required levels of trust to access a system or a privileged account.
Just-in-time provisioning: Provides temporary access to privileged users only when needed, reducing the risk of unauthorized access.
Session isolation with sensitive data masking: Implements agentless and proxy-based session isolation between users and target systems. Isolates database sessions, tracks and controls all user activities, and prevents exposure of sensitive data with on-the-fly data masking.
Secure remote access: Ensures fast, easy, and secure privileged access for remote users needing to access the organization’s internal resources on a controlled and temporary basis. Eliminates the need for VPN clients or security agents, streamlining operations and reducing potential vulnerabilities.
Adaptive Multi-Factor Authentication: Enhances security by requiring multiple forms of verification and AI-based user behavior factors in authentication before granting access.
Accountability and audit trails: Enables personal accountability while using shared credentials and provides a track record of any privileged user activity and session with video and event-based logs for forensic investigations.
Anomaly and threat intelligence: Continuously analyzes real-time activity with a baseline built to identify the unusual behavior of a user and indications of a possible attack.
Conclusion and Urgent Call to Action: Deadline: October 17, 2024
The scope of NIS2 regulations has expanded to cover companies over 15 sectors with more than 50 employees and over €10m in revenue. This means that almost 150,000 companies in the EU will now need to comply with these regulations. Applicable organizations must take steps to prepare for the compliance journey sooner rather than later is crucial. Reach out to us to receive assistance from PAM experts in evaluating your privileged access management practices as you prepare for NIS2.
If you want to protect your organization against cyber threats and get a solution capable of adapting to the latest insights, you may start using Kron PAM, one of the world's leading PAM products. With it’s comprehensive PAM solutions Kron recognized in the reports of Gartner, KuppingerCole, Omdia, and Forrester, which protects your organization against data breaches in the best way with top-level access security.
You can contact us to get more detailed information about Kron PAM, which provides excellent security for your entire technical infrastructure.
Highlights
Other Blogs

How Edge Computing Will Drive New Demands for Data Security, Infrastructure Integrity and New IT Policies

Solving the Privileged Access Management Challenge in Dynamic Cloud Environments


















