
Safeguard Your AI Future: How Kron PAM Secures MCP Servers with Zero Machine Identity Exposure
Apr 22, 2025
/
Erhan YILMAZ
AI agents and applications are changing how companies run in the fast-changing digital environment of today. AI is at the core of invention, from streamlining processes to improving decision-making. But with great power comes great responsibility—particularly when it comes to securing sensitive credentials. The rise of Model Context Protocol (MCP) servers, which connect to target resources like databases, servers, and applications to execute tasks, has introduced a critical vulnerability: credential exposure.
The numbers paint a stark picture. A study by Cybersecurity Ventures revealed that 80% of organizations experienced at least one breach due to mismanaged credentials in the past year. Static credentials—such as passwords, API keys, or SSL certificates—stored directly on MCP servers are a ticking time bomb. If these credentials fall into the wrong hands, the consequences can be catastrophic, leading to unauthorized access, data leaks, and reputational damage.
The Problem: Static Credentials in MCP Servers
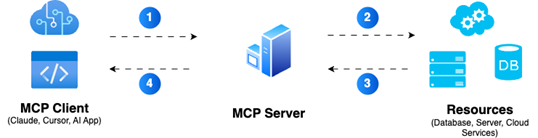
Let’s break down the issue with a simple flowchart:
- An AI agent requests access to a target resource.
- The MCP server uses static credentials (e.g., a hardcoded password) to authenticate.
- The target database or application grants access.
- The task is completed, but the static credentials remain exposed on the MCP server, vulnerable to theft or misuse.
Let's examine the code within the AI application. The database username and password are exposed and accessible to anyone.
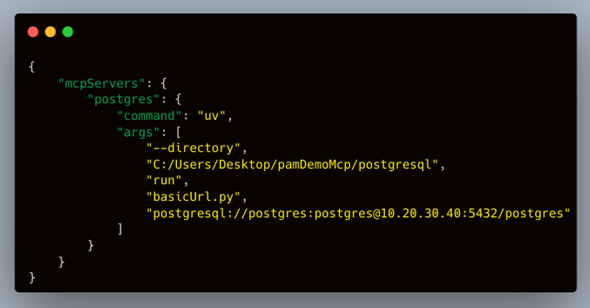
This approach is a security nightmare. Static credentials are often left unchanged for months or even years, making them an easy target for cybercriminals. Worse, if an MCP server is compromised, every resource it connects to is at risk.
The Solution: Kron PAM’s Secure Credential Management
Enter Kron PAM—a game-changing Privileged Access Management (PAM) solution designed to eliminate credential exposure and secure your AI-driven operations. Kron PAM integrates seamlessly with MCP servers to provide a dynamic, vault-based approach to credential management. Here’s how it works, as shown in the second flowchart:
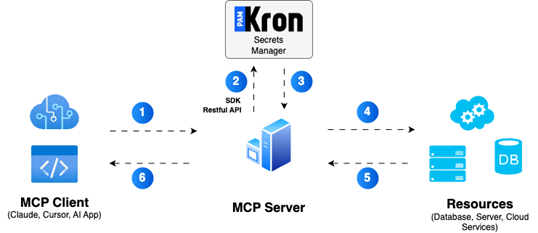
This is how Kron PAM secures secrets in MCP Servers:
- An AI agent requests access to a target resource.
- The MCP server sends a request to Kron PAM’s Secrets Manager.
- Kron PAM securely retrieves the necessary credentials (e.g., a password or API key) and provides them to the MCP server.
- The MCP server uses these credentials to authenticate the target resource.
- The task is completed, and the credentials are never stored on the MCP server—they remain safely in Kron PAM’s vault.
- The AI agent receives the results, and the process repeats securely for future requests.
Now, let's consider the scenario where Kron PAM is utilized. The account name registered in Kron PAM and Secrets Manager security token are used in place, instead of writing the database username and password. This ensures that a malicious insider threat or external hacker accessing the code cannot directly obtain the password.
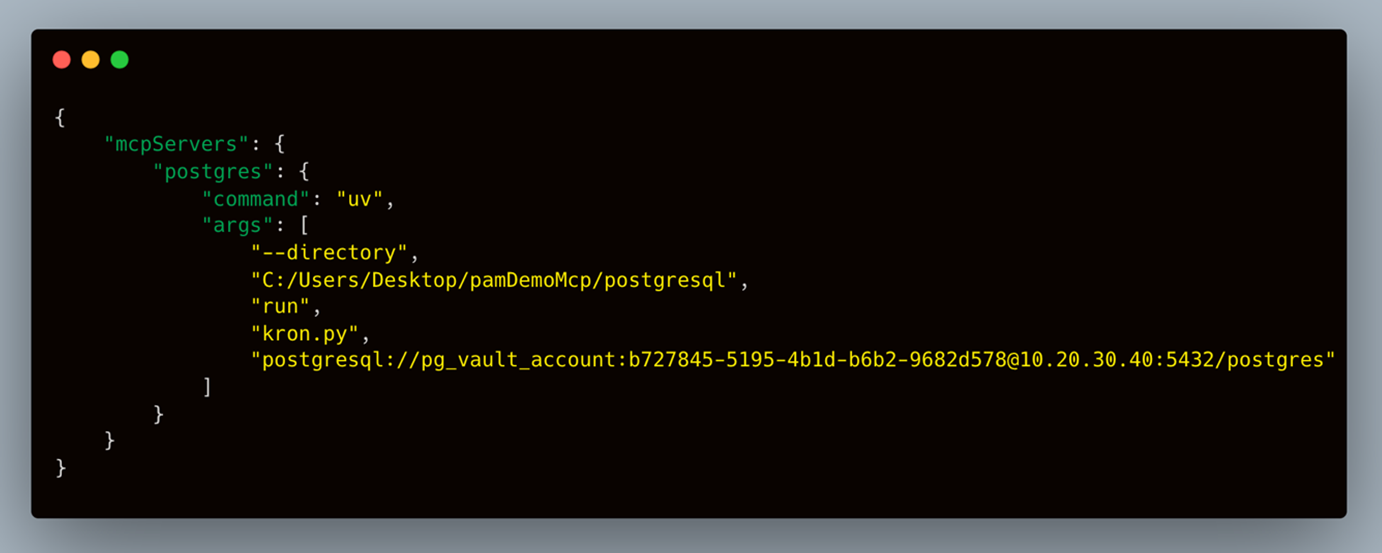
Take a look at the MCP server. Passwords can be securely accessed by authorized apps using Kron PAM's flexible Rest API or user-friendly SDKs. Machine identities are managed and rotated periodically by Kron PAM instead of static passwords that are hardcoded in the source code.
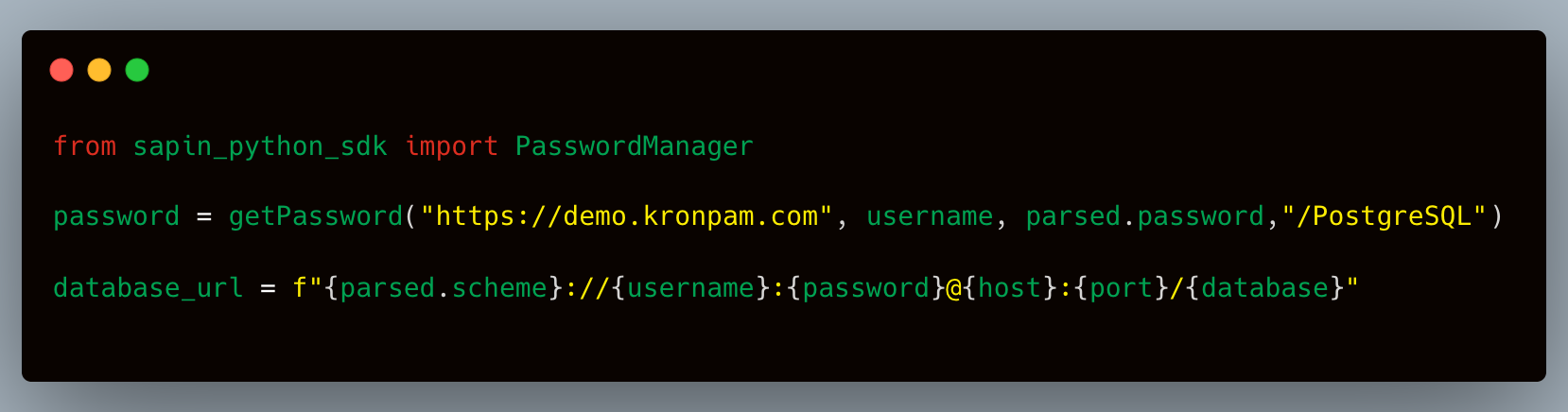
By storing sensitive secrets like passwords, API keys, and SSL certificates in Kron PAM’s encrypted vault, MCP servers no longer need to hold static credentials. Instead, they fetch credentials dynamically as needed, ensuring zero exposure and maximum security.
Key Benefits of Kron PAM for MCP Servers
- Eliminate Credential Exposure: With Kron PAM, sensitive credentials are never stored on MCP servers, drastically reducing the risk of theft or misuse.
- Enhanced Security for AI Operations: Protect your AI agents and applications from unauthorized access, ensuring your data remains safe.
- Compliance Made Easy: Kron PAM helps you meet stringent regulatory requirements (e.g., GDPR, HIPAA) by enforcing secure credential management practices.
- Scalability for the Future: As your AI-driven operations grow, Kron PAM scales effortlessly to secure an increasing number of MCP servers and resources.
- Peace of Mind: Focus on innovation, not security threats, knowing that Kron PAM has your back.
Conclusion: Secure Your AI Future with Kron PAM
The rise of AI agents and MCP servers has unlocked incredible opportunities for businesses—but it has also introduced new security challenges. Static credentials stored on MCP servers are a weak link that cybercriminals are eager to exploit. With Kron PAM, you can break this link for good. By securely managing credentials in a centralized vault, Kron PAM ensures that your MCP servers operate with zero credential exposure, protecting your organization from costly breaches and empowering you to innovate with confidence.
Don’t let credential exposure hold your AI future hostage. Embrace Kron PAM today and take the first step toward a secure, AI-driven tomorrow.
*Written by Erhan YILMAZ. He is a PAM Product Management Director at Kron.
Highlights
Other Blogs




















