
Secrets Management Simplified: Protecting Credentials with Kron PAM
Mar 12, 2025
/
Furkan KIRMACI
Hardcoded credentials pose a significant security risk in software development. When application secrets such as API keys, database credentials, or encryption keys are stored directly in source code or configuration files, they become vulnerable to exposure through version control systems, insider threats, and unauthorized access. Attackers actively scan public repositories for leaked credentials, and even private repositories are not immune if access controls are insufficient.
Secret management mitigates these risks by centralizing and dynamically injecting credentials into applications at runtime. This ensures that secrets remain encrypted, access-controlled, and auditable, reducing the attack surface while maintaining operational efficiency.
Secret management is essential in the following areas:
- API-Driven Applications: Services communicating with external or internal APIs require authentication, and storing API keys securely is crucial.
- Containerized Applications: In OpenShift and Kubernetes environments, secrets must be dynamically injected rather than embedded in images.
- CI/CD Pipelines: Build and deployment processes often require credentials, which should be managed centrally instead of stored in scripts.
- Infrastructure as Code (IaC): Terraform, Ansible, and other automation tools frequently use sensitive credentials, which should be securely retrieved at runtime.
- Microservices and Service Meshes: Services communicating within a cluster should retrieve authentication tokens securely to prevent unauthorized access.
How Kron PAM Secret Management Solves the Problem?
Kron PAM provides a comprehensive solution for secure secret management through its SDKs for Java, .NET, Python, and C++. It enables authentication-based access to credentials without exposing them in the application code. Below are the specific methods for integrating Kron PAM Secret Management in different environments.
Authentication-Based Secret Retrieval
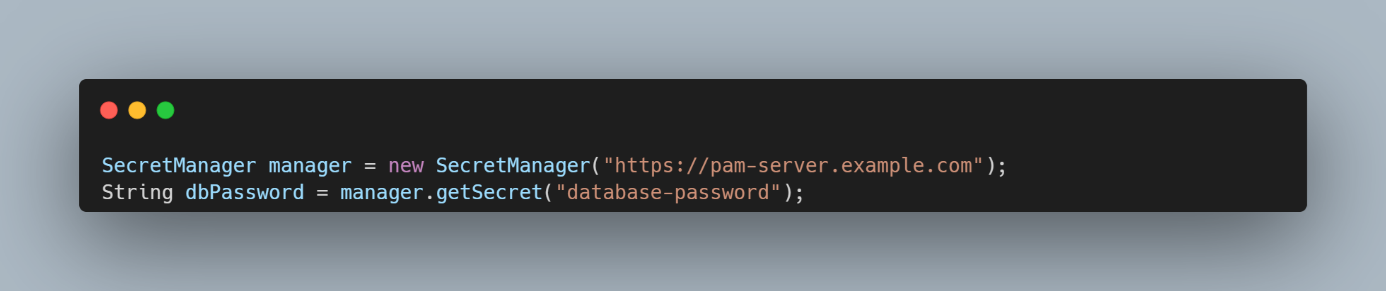
- Java SDK: Using Kron PAM Java SDK, applications can authenticate via the Kron PAM AAPM Agent and retrieve secrets using API calls.
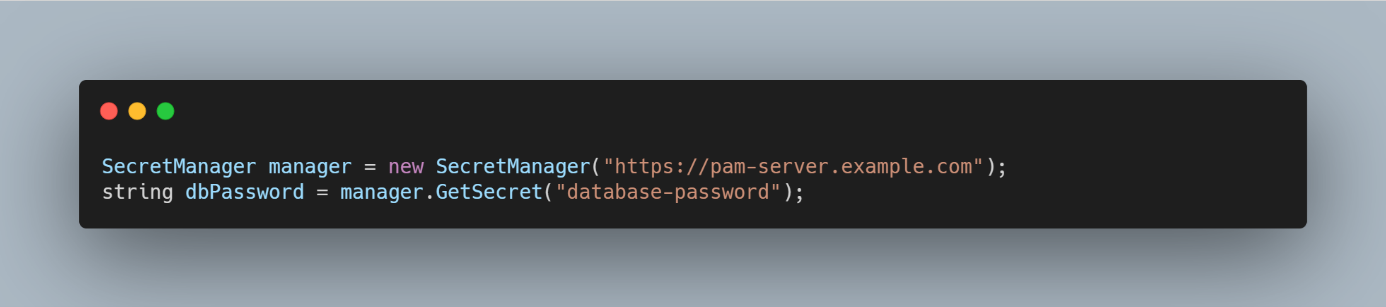
- .NET SDK: The .NET SDK provides similar capabilities for retrieving secrets securely.
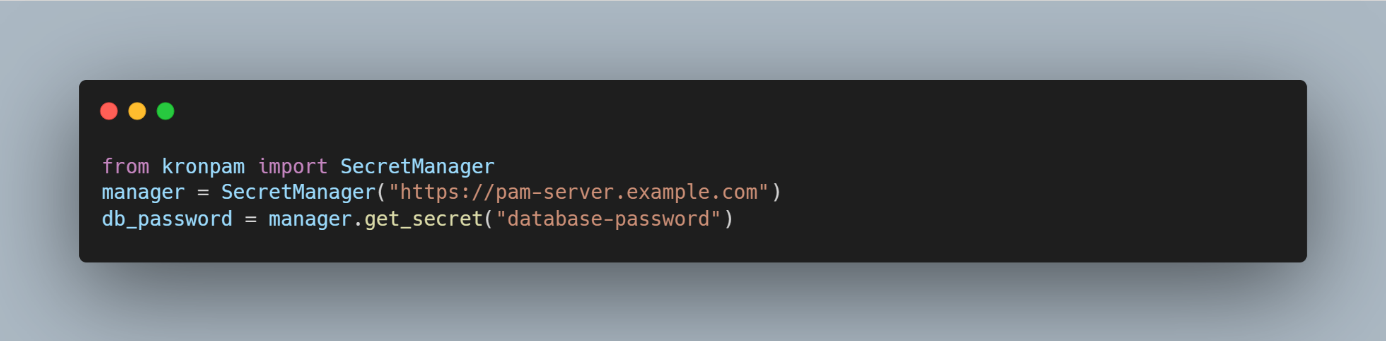
- Python SDK: Python applications can use the SDK to securely fetch credentials.
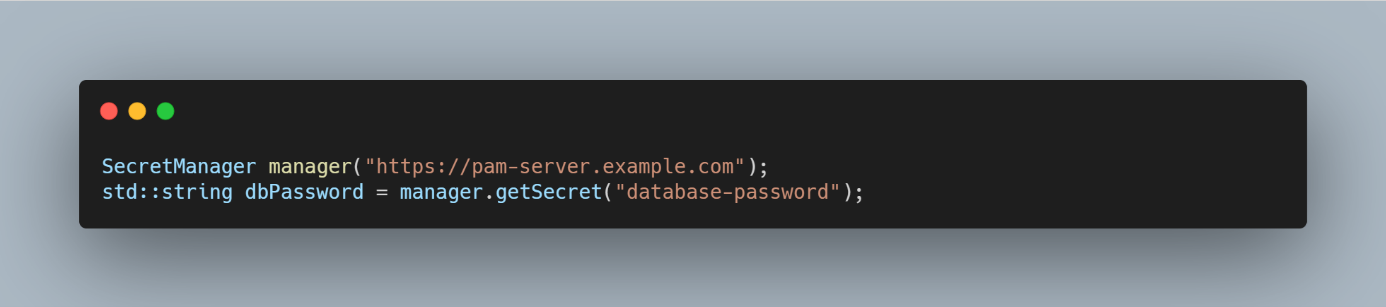
- C++ SDK: The C++ SDK allows for seamless integration with native applications.
Replacing Hardcoded Credentials in OpenShift & Kubernetes
In Kubernetes and OpenShift environments, Kron PAM eliminates hardcoded credentials using two different methods: Password Service and Sidecar Container Approach.
- Password Service Method
- The Kron PAM Password Service provides dynamic, on-demand credential retrieval.
- Applications request credentials directly from the Password Service via secure API calls.
- This method ensures that secrets are retrieved securely at runtime and never stored statically within the application.
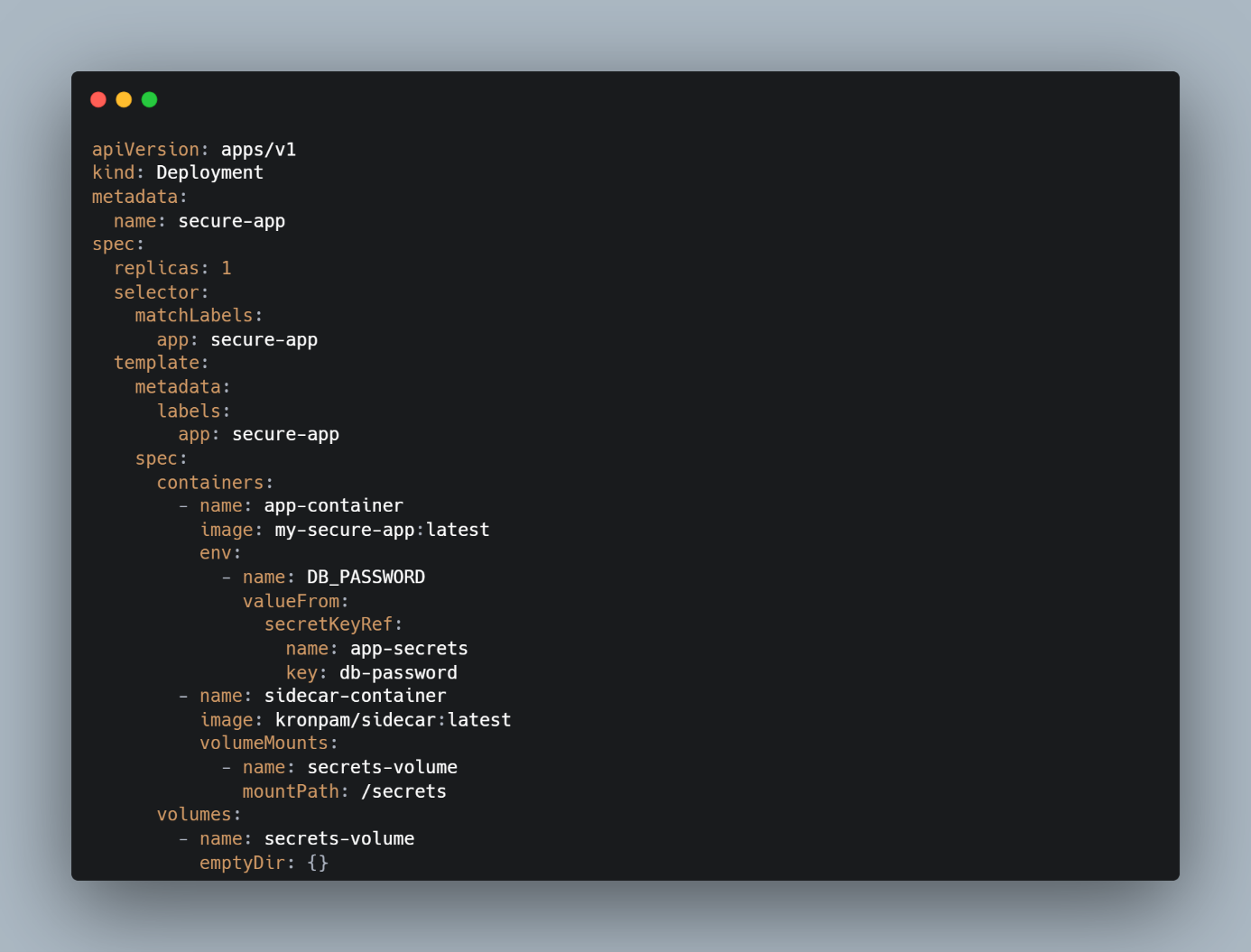
- Sidecar Container Method
- The Application Token Agent (AAPM Agent) and Sidecar Container are deployed as separate containers within the same pod.
- The AAPM Agent retrieves secrets from Kron PAM.
- The AAPM Agent and Sidecar Container communicate via secure channel to securely transfer secrets.
- The Sidecar Container injects the retrieved secrets into the application’s environment.
- Applications access credentials via environment variables or volume-mounted files.
Configuring the AAPM Agent and Sidecar Container
- Deploy the AAPM Agent and Sidecar Container alongside the application in a Kubernetes pod.
- Define the necessary volume mounts and environment variables for secret retrieval.
- Ensure secure channel communication between the AAPM Agent and Sidecar Container.
Automated Secret Rotation
- Kron PAM supports automatic secret rotation.
- The AAPM Agent retrieves updated credentials and transmits them securely via secure channel to the Sidecar Container.
- Applications receive updated secrets without requiring a restart.
Conclusion
Hardcoded credentials introduce security vulnerabilities that can be exploited by attackers. Kron PAM Secret Management provides a secure, authentication-based solution for API-driven applications using Java, .NET, Python, and C++ SDKs. In Kubernetes and OpenShift environments, organizations can choose between Password Service for direct API-based retrieval or the Sidecar Container Method for dynamic secret injection. By integrating Kron PAM, organizations can enhance security, ensure compliance, and streamline secret management in dynamic and cloud-native environments.
*Written by Furkan KIRMACI. He is a Senior Product Owner at Kron.




















